Implement Code Scanning with Pipelines¶
The source code in the code repository, as the original form of software, its security flaws are the direct root cause of software vulnerabilities. Therefore, discovering security flaws in the source code through code scanning analysis is an important method to reduce potential vulnerabilities in software.
For example, SonarQube is an automatic code review tool used to detect bugs in project code and improve test coverage. It can be integrated with existing workflows in the project for continuous code checks between project branches and pull requests.
This article will introduce how to integrate SonarQube into the pipeline to implement code scanning capabilities.
Integrate SonarQube by workspace¶
Please ensure that you have a SonarQube environment and that it is network-connected with the current environment without any problems.
-
Enter the Toolchain Integration page, click the Toolchain Integration button.
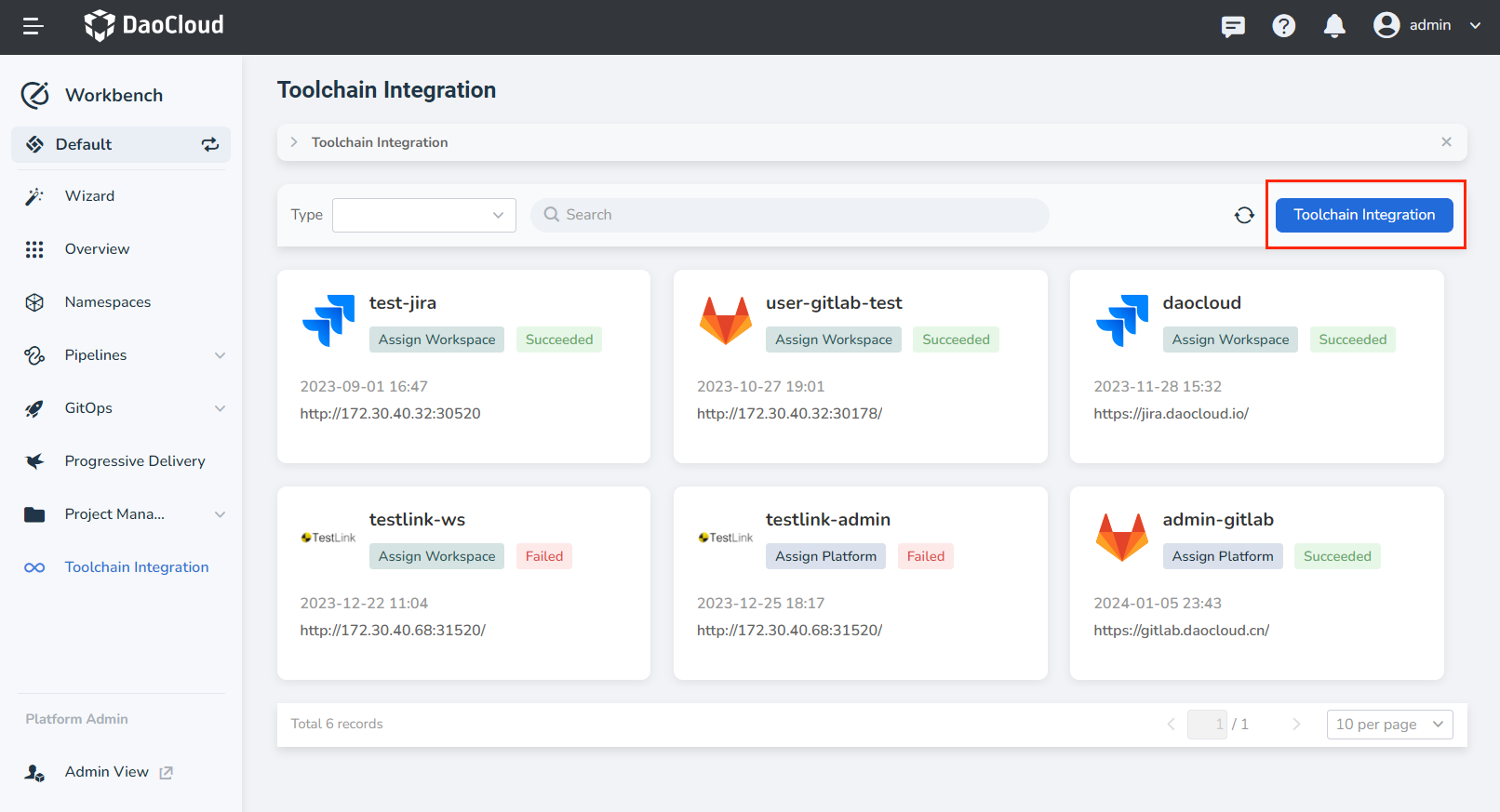
-
Refer to the following instructions to configure the relevant parameters:
- Tools: Choose a toolchain type for integration.
- Integration Name: The name of the integrated tool, must not be duplicated.
- SonarQube Address: The address that can access the toolchain, starting with a domain name or IP address that starts with http://, https://.
- Token: Generate an administrator token (Token) in SonarQube, the operation path is: My Account -> Profile -> Security -> Generate -> Copy
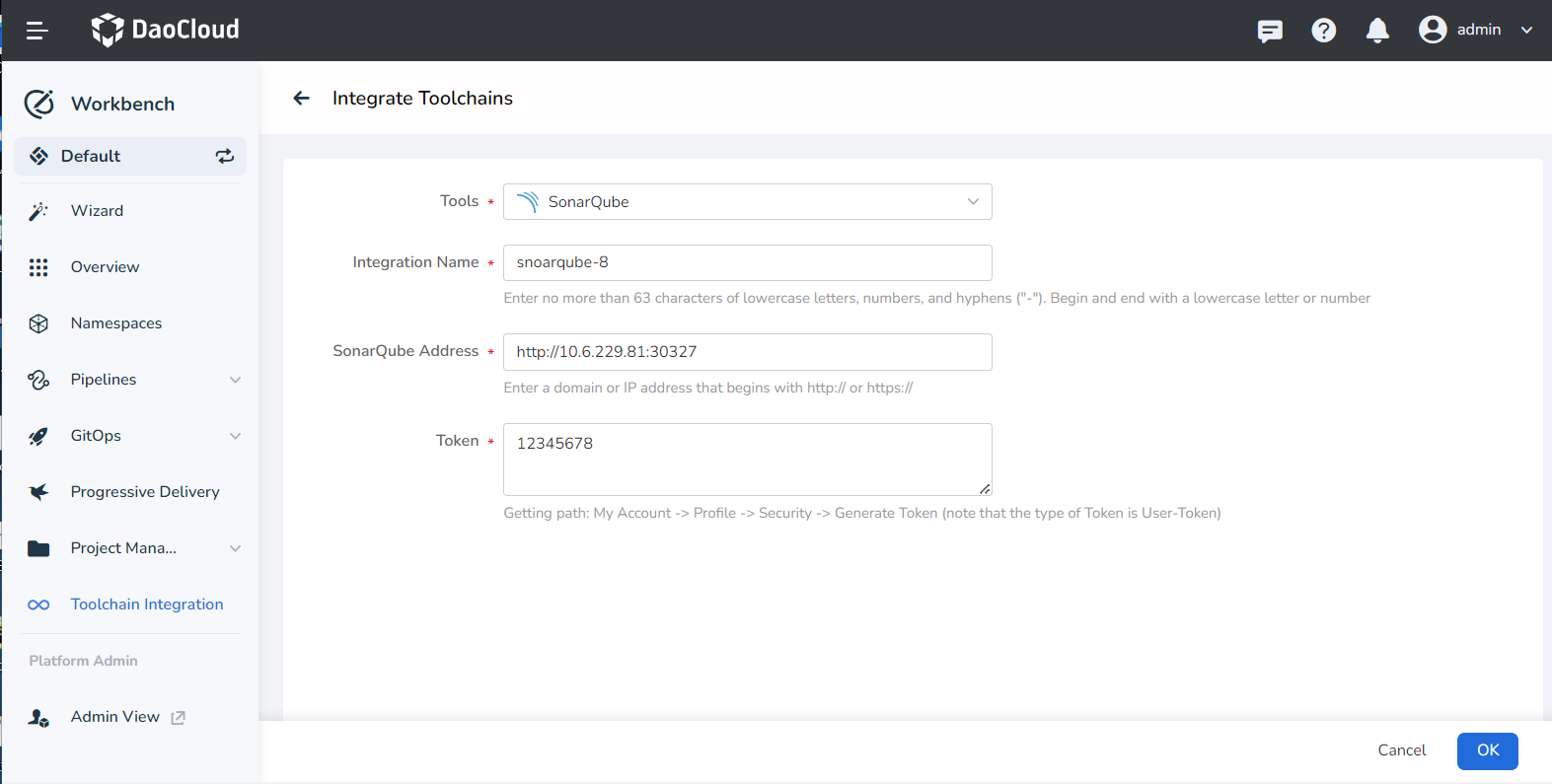
-
Click OK to return to the toolchain list page after successful integration.
Creating a pipeline¶
-
On the pipeline page, click Create Pipeline.
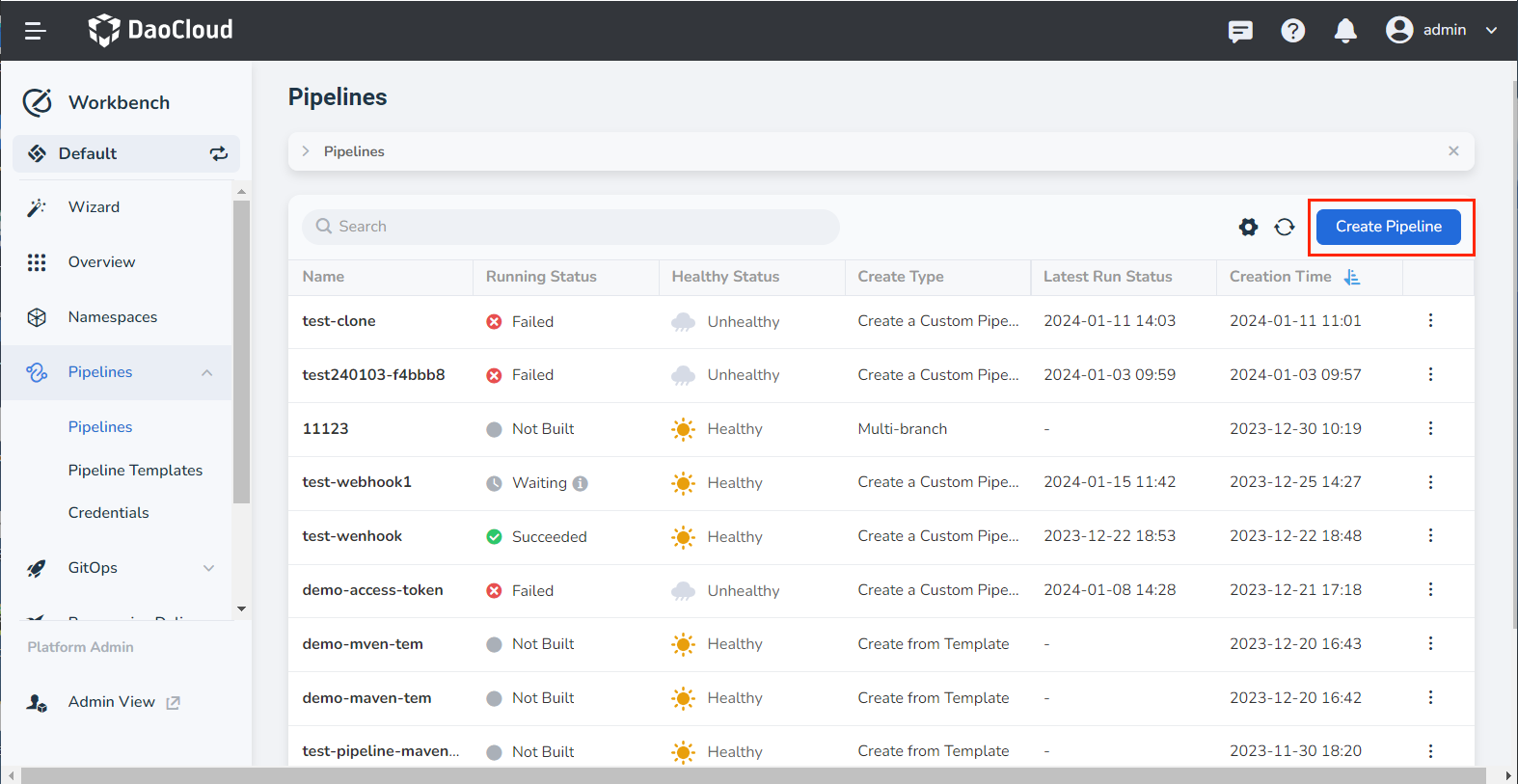
-
Choose Create a custom pipelines.
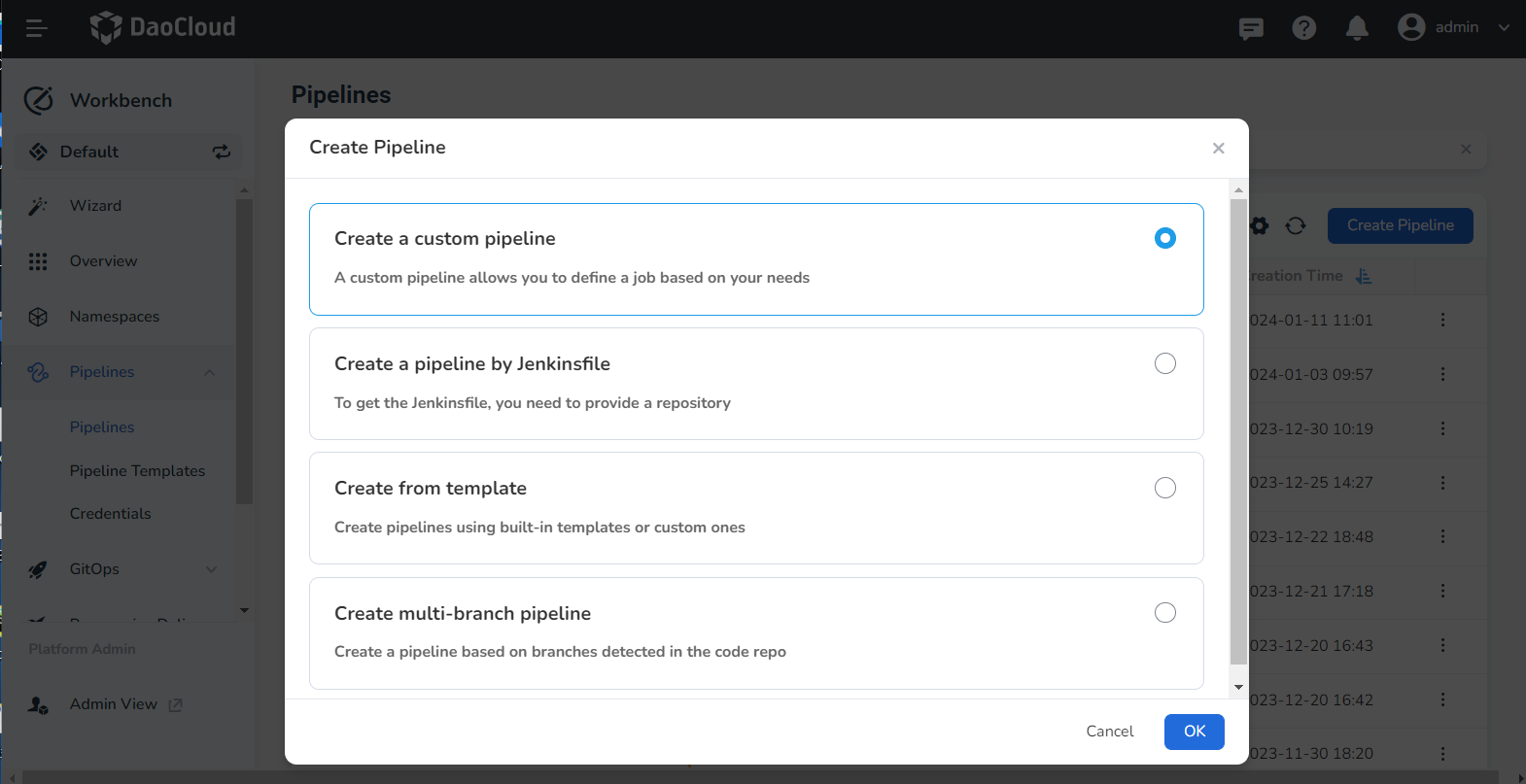
-
Enter a name, use the other default values, and click OK.
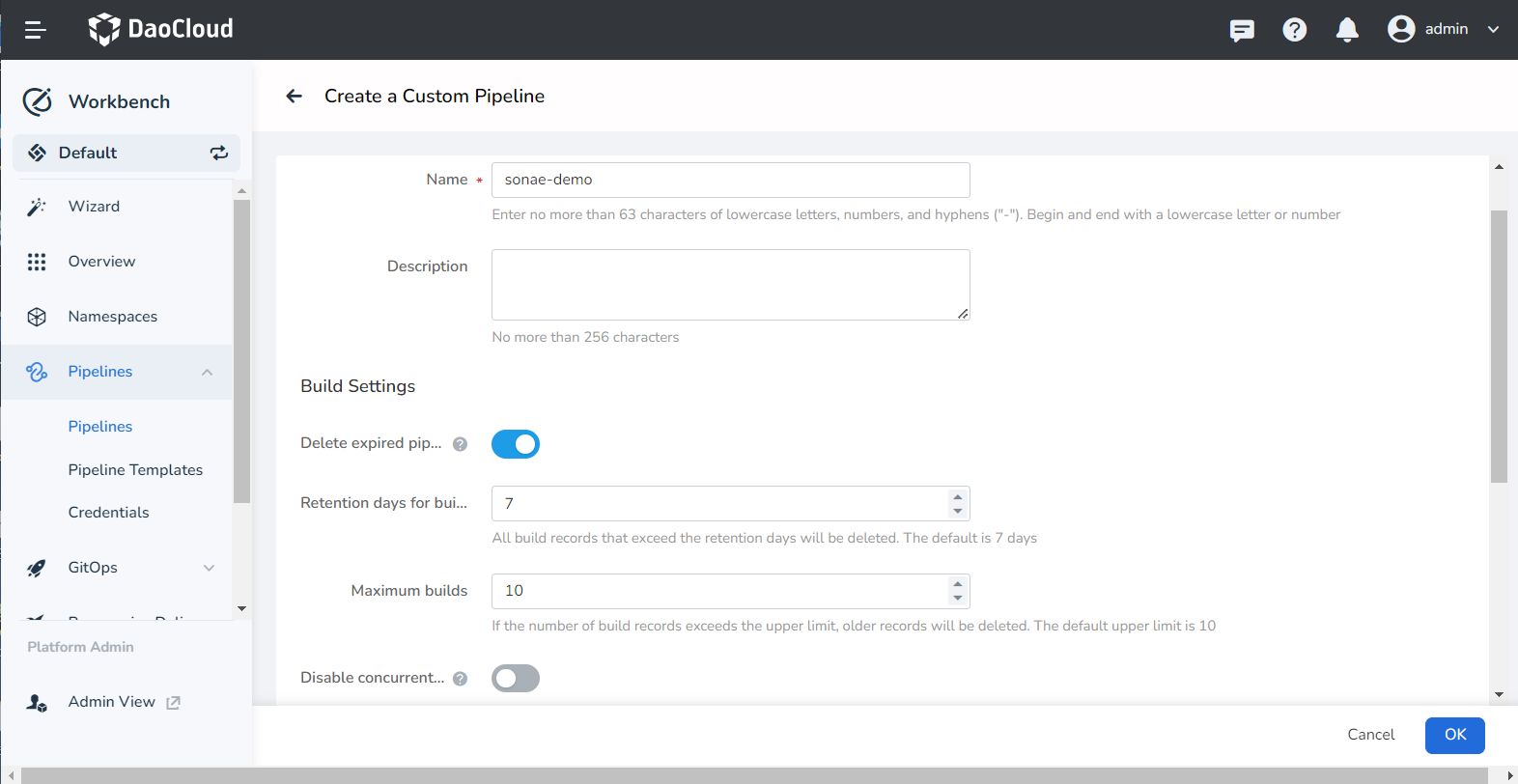
Editing pipeline¶
-
Click a pipeline to enter its details page, and click Edit Pipeline in the upper right corner.
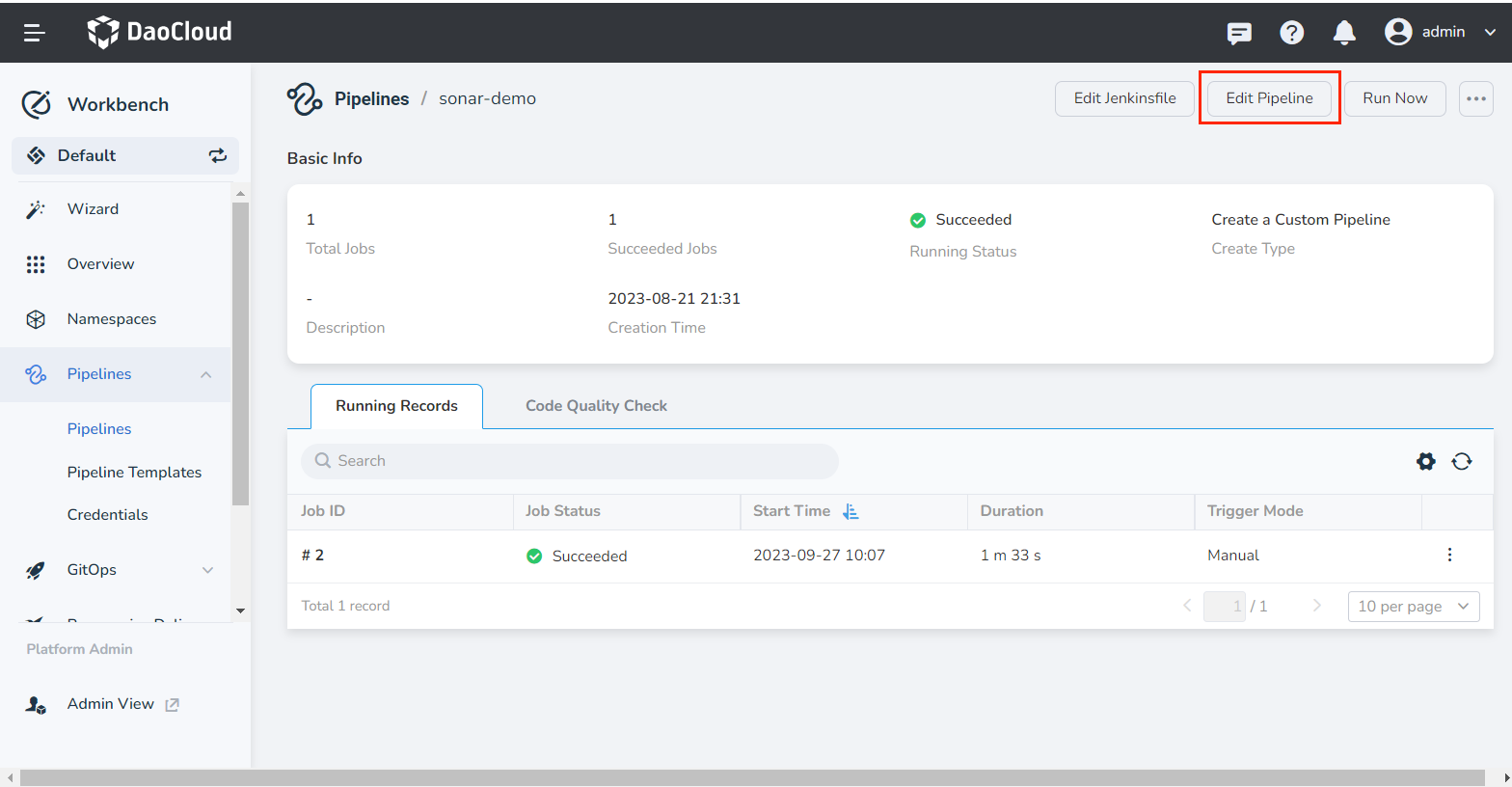
-
Configure global settings:
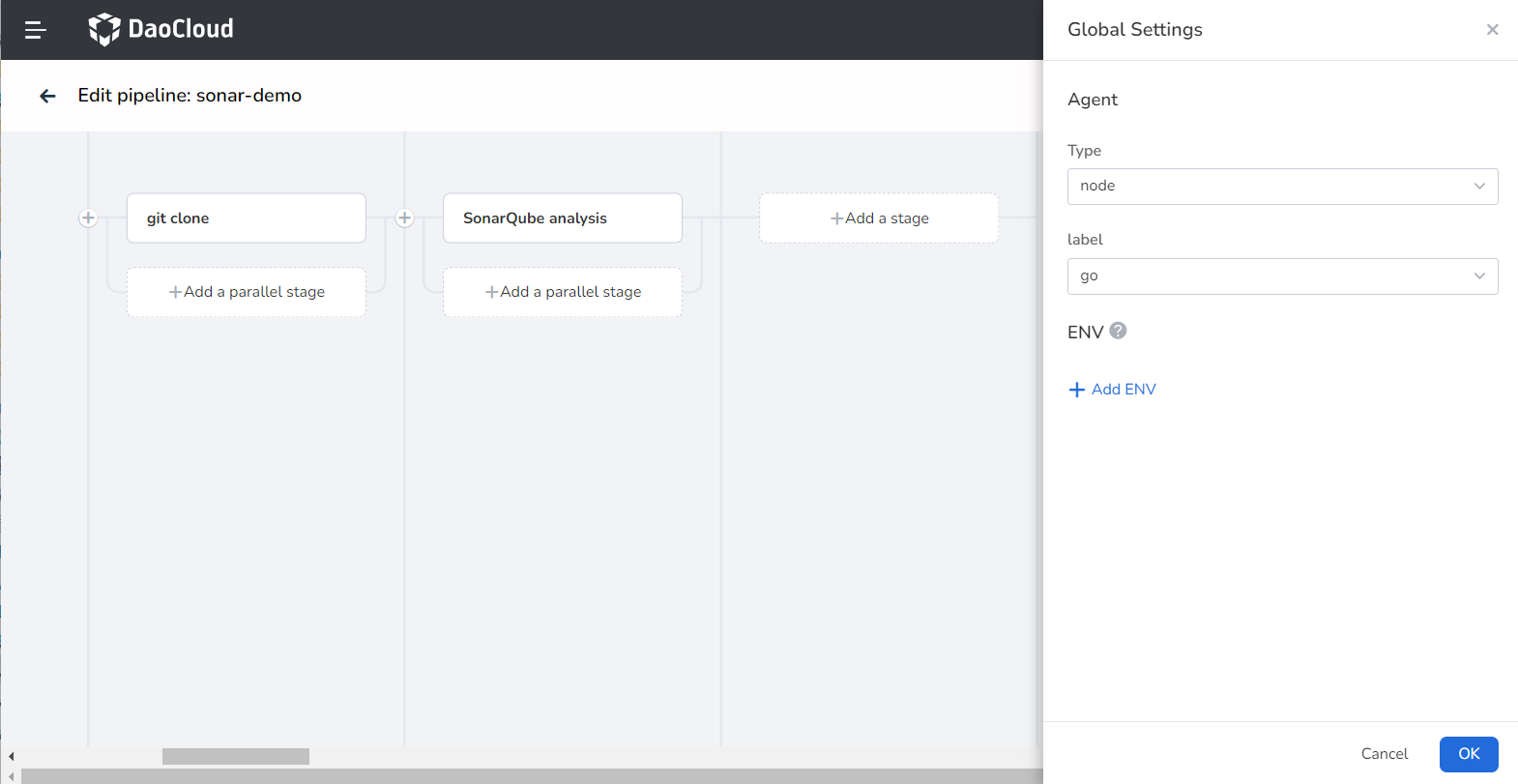
-
Define stage one git clone in the graphical interface as follows:
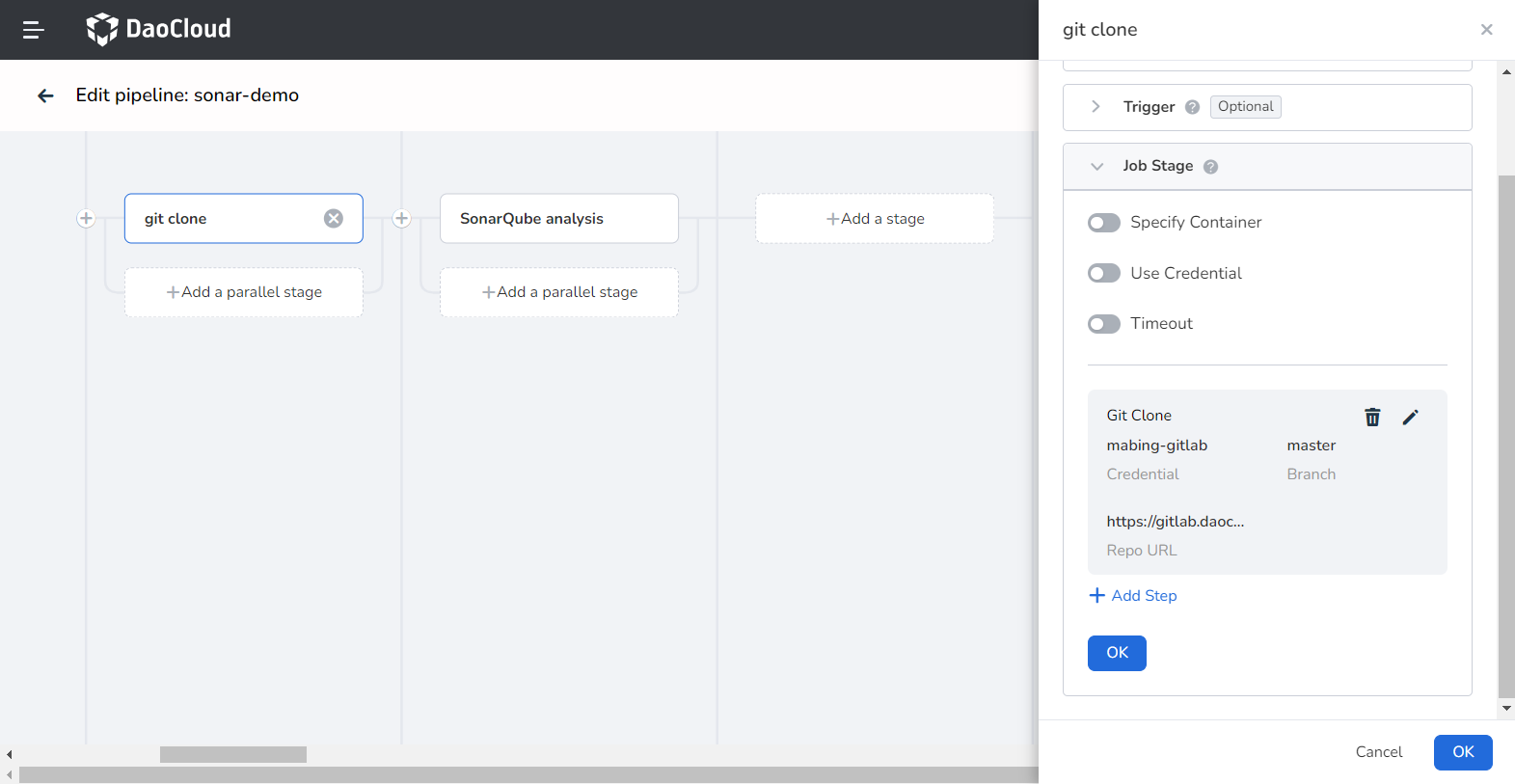
-
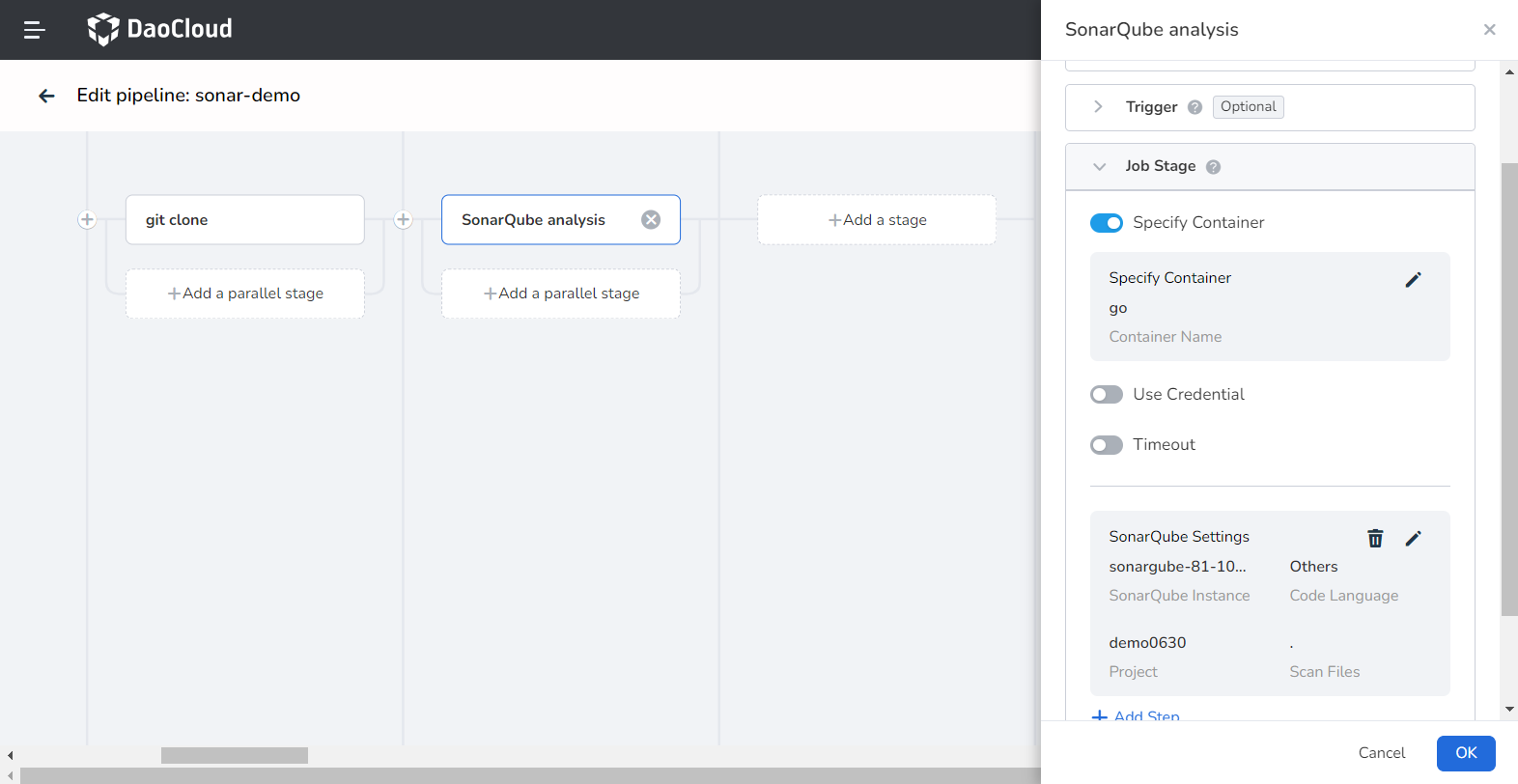
Define stage two SonarQube analysis in the graphical interface as follows:
-
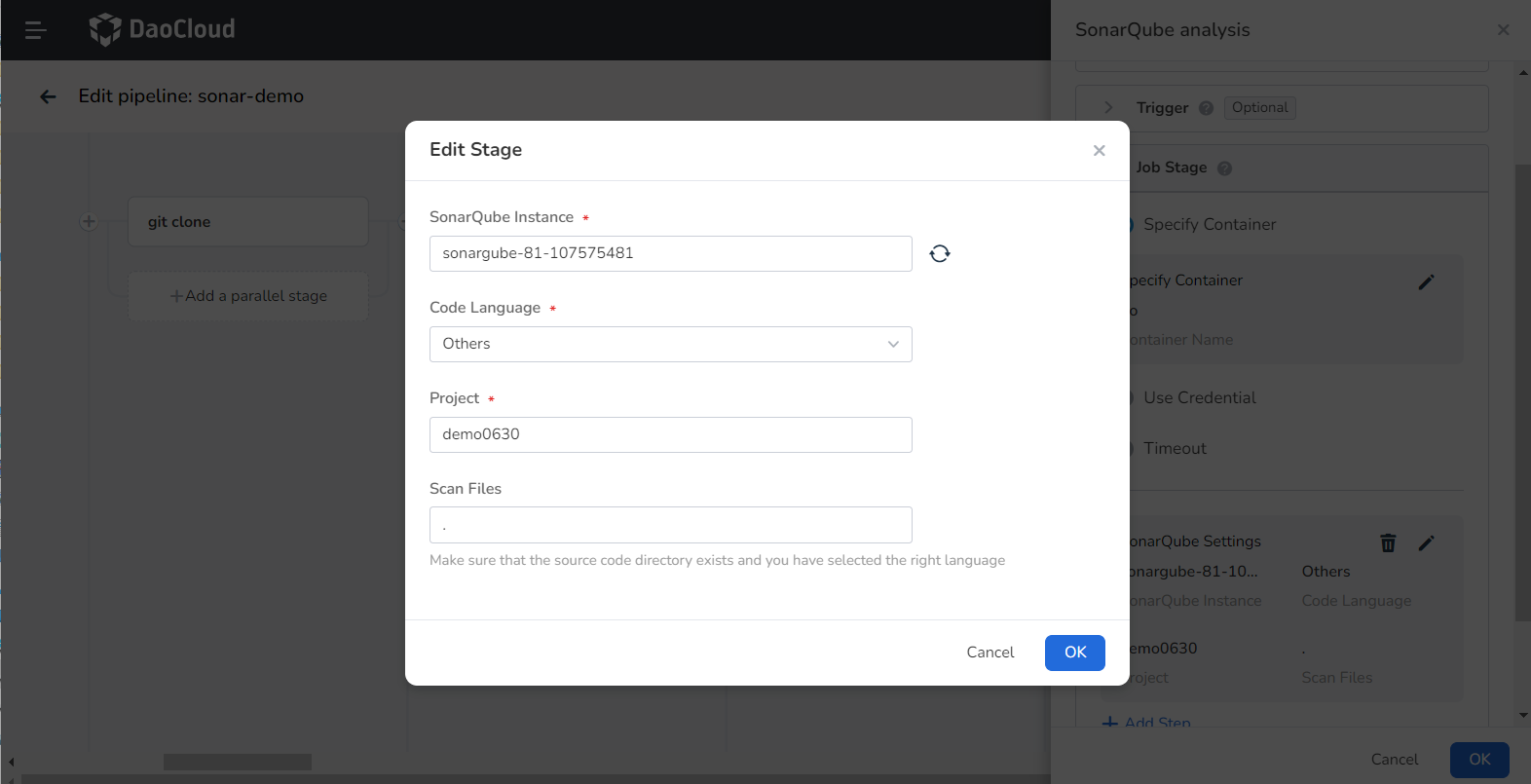
SonarQube Instance: Select the SonaQube instance integrated in the above steps.
- Code Language: Since different code languages correspond to different SonaQube scan commands, if the language is Java, please select Maven, otherwise select others. In this example, we choose others.
- Project: Define the project to be scanned in SonarQube
-
Scan Files: The directory address of the file in the code repository that needs to be scanned
-
Save and immediately run the pipeline, and wait for the pipeline to run successfully.
Viewing code scanning results¶
-
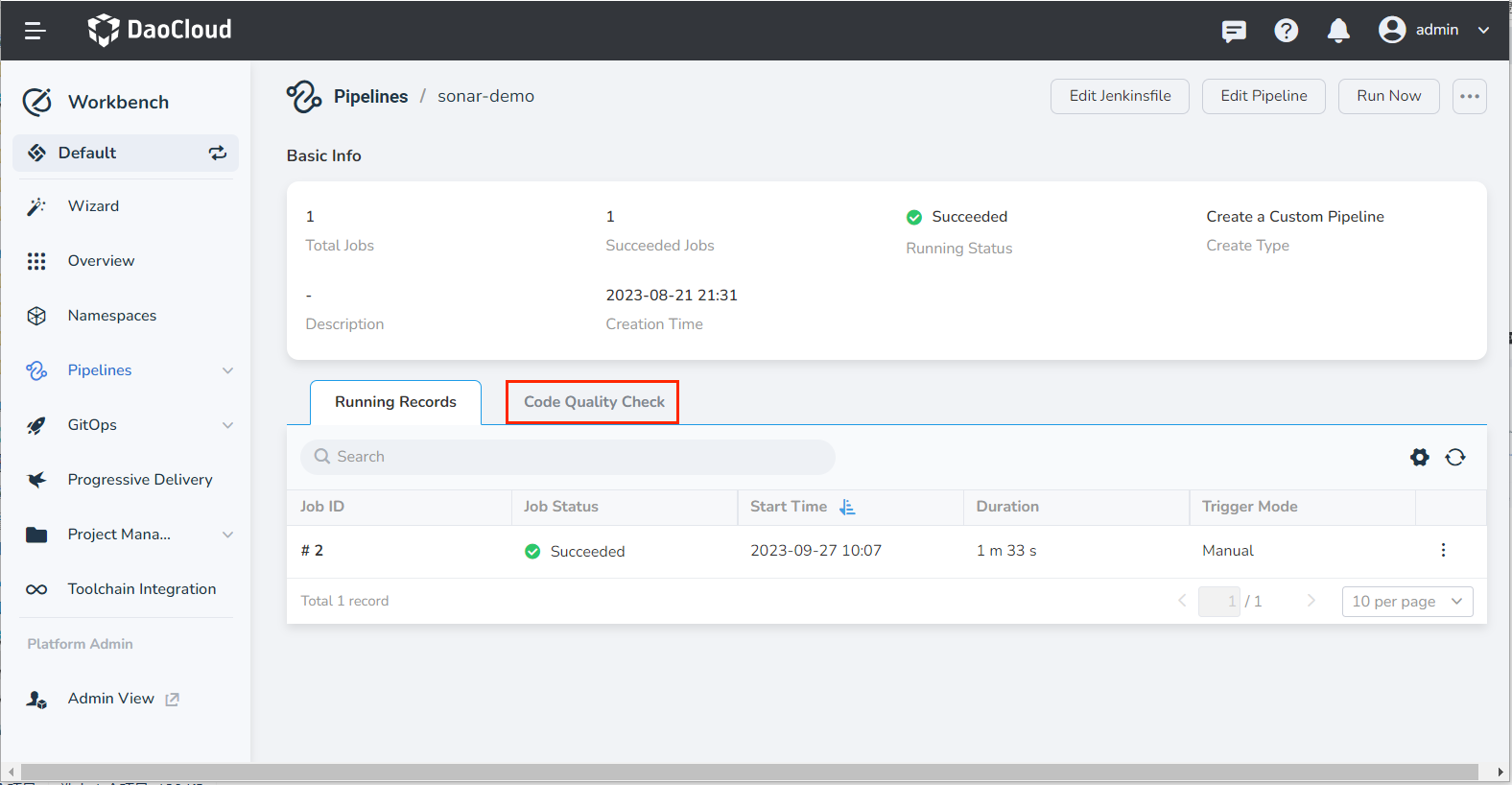
After the pipeline runs successfully, click Code Quality Check on the pipeline details page.
-
View the code scanning results, click View More to go to the SonarQube backend to view more scanning information.